Tailscale Exit Nodes

Tailscale
If you've never heard of Tailscale, let me give you the quick summary.
Tailscale, at its heart, is a VPN - and not just the ones you see spammed about on the internet to protect your privacy. Rather, it's a way to get all your various computers, servers, and even phones sharing a network so that you don't need to traverse the public internet to connect to them. Tailscale leverages the Wireguard protocol, is open source, and is free for small, personal setups - which makes it perfect for me.
I have a few VPSes all over the place - I have some at Digital Ocean - Referral Link, Contabo for my personal git, and 1984 for my Iceland-based servers. In addition I am embarassed by the number of laptops, desktops, and Pi's I have. But, before Tailscale, they were all over the dang place on how to connect - I even ssh'ed into my Git server over public internet (though with keys and not passwords - I am not a monster).
So, what I learned was that I could connect them all and create a mesh with Tailscale, a few below -
Since they were all networked, I could connect to Idris by simply going ssh mjh@idris and the MagicDNS feature would alias the internal IP (something like 10.100.x.x) to a name - and let me continue to log in. It's pretty slick for both aliases and not traversing the world to connect to my various machines. A few more settings and you cannot connect to my boxes without being on my Tailnet - unless you are on my network, https://tones.nalth.is/ doesn't actually connect to anything.
In the spirit of automating everything, anytime I create a new Contabo server, I simply allow it to build it with a cloud-init template I wrote:
This sets up the server with GitHub SSH keys, installs Tailscale, configures it to an Tailscale Auth Key, and allows Tailscale through the firewall. (It also disables root user login and adds my username as a sudo user - makes my life at lot easier).
You can even use it with Gitpod meaning that when I am working from my iPad I can connect into my Tailnet with ephemeral nodes and a key in my environment variables. However, how I use Gitpod on the road with my various services is another blog post for another day.
All of this lets me treat all my devices as though they are networked whether they are in my apartment, in Reykjavik, or wherever my phone happens to be.
Coffee Shops and VPNs
If you go search for "VPN" you'll find a million ads and "reviews" (which are just ads in disguise) for VPNs to protect your security. Although I use ProtonVPN on new devices or devices that I may not want on my personal network (such as client devices), Tailscale is on everything. Using a VPN from those advertised ones are mostly about hiding your traffic from those providing internet, such as coffee shops, airports, or company lobbies. This, in and of itself, is very good and very important!
However, this is not what VPNs are for and I already have one through my Tailnet. So, why add another tool to the mix when I can get Tailscale to do this?
ProtonVPN and others aren't necessarily providing the VPN aspect of networking your devices but rather where your traffic is routed and exits. Where it "exits" tells internet services where you are "at". When ProtonVPN says "Chicago" it's saying your traffic is going to the public internet from a machine sitting in Chicago .
However, Tailscale has exit nodes. This means I can keep a tiny machine that simply runs Tailscale out on 1984 for when I need to connect to Icelandic resources and my Contabo exit node in Chicago for most things. This lets me simply hit a button and have an exit node while on public networks and have my traffic routed entirely somewhere else. In fact, as I am sitting in a quiet coffee shop, I was streaming a bit of Icelandic music and simply used my "Reykjavik" exit node - and my IP shows as my VPS IP out in Iceland, and definitely not as this nice little coffee shop. However, I can simply enter my exit node list and switch to something more local - the website for my credit union doesn't like it when it thinks I am connecting from Iceland!
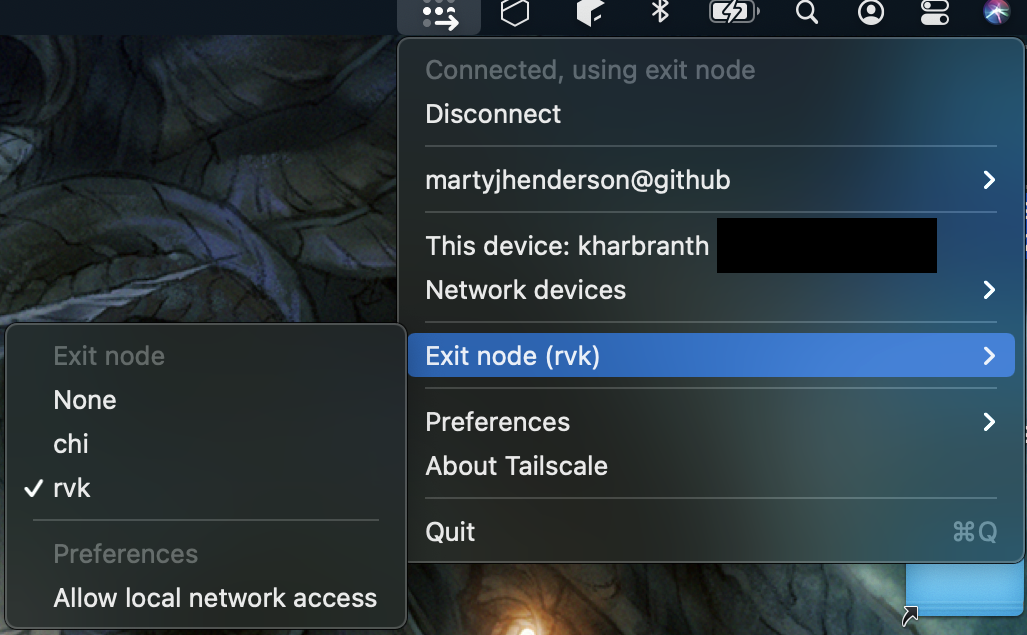
(For my ease, I use the shorthand "rvk" for Reykjavik and "chi" for Chicago servers)
My taking my existing tailnet and adding on two cheap VPS as exit nodes, I have my own security VPN that works nicely in coffee shops as well as ensures that I can connect to my personal git servers. Reducing tools without reducing security is something I am trying to focus on this year, so I hope that this is one step.
I hope you get a chance to play with Tailscale and find more uses! Let me know if you find something creative out there!

